Facts About Safety Network Revealed

If there is any kind of functional need on an opposing stage with the hold input de-energized, and with all periods timed out, the controller device breakthroughs into the yellow adjustment interval as well as does not recycle the stroll on that stage until those needs have actually been offered - Traffic control signs. Phase Leave out Command which creates noninclusion of a phase, even in the presence of demand, by the application of an outside signal, hence impacting phase choice.
The phase to be left out does not send a clashing phone call to any kind of other stage yet accepts and shops telephone calls. The activation of Phase Omit does not impact a phase in the process of timing. Pedestrian Omit Command which hinders the selection of a phase arising from a pedestrian contact the subject phase, as well as it bans the maintenance of that pedestrian call.
After the beginning of the subject stage green, a pedestrian phone call is serviced or reused only in the absence of a serviceable contradictory call and also with Pedestrian Omit on the phase non-active. Activation of this input does not impact a pedestrian motion in the process of timing. Input Summary Force-Off Command which supplies for the discontinuations of environment-friendly timing or WALK hold in the non-actuated setting of the energetic stage in the timing ring.
Not known Incorrect Statements About Safety Network
The Force-Off is ineffective during the timing of Initial, stroll or pedestrian clearance. Force-Off is effective just as lengthy as the input is maintained. Red Rest Calls for the controller unit to relax in red in all phases of the timing ring(s) by continuous application of an outside signal. The enrollment of a functional contradictory telephone call results in the instant advance from Red Relax to eco-friendly of the demanding stage.
The enrollment of a serviceable phone call on the energetic phase prior to entrance right into the Red Rest state despite having this signal used, outcomes (if Red Revert is active) in the extension of the termination of the active phase with appropriate yellow change period and Red display screen throughout selected in Red Revert. https://www.polygon.com/users/s4fetynetw0rk.
Inhibit Maximum Termination Disables the maximum termination functions of all stages in the picked timing ring. This input does not, nevertheless, prevent the timing of Maximum Eco-friendly. Omit Red Clearance Triggers the omission of Red Clearance timing intervals Pedestrian Recycle Controls the recycling of the pedestrian movement. The procedure relies on whether the stage is running in the activated or non-actuated mode: In the activated setting, if a serviceable pedestrian telephone call exists on the subject as well as the Hold input is energetic, the pedestrian activity is reused when the Pedestrian Recycle input is energetic, no matter of whether a functional conflicting phone call exists.
What Does Safety Network Do?
Quit Timing When triggered, causes cessation of controller system ring timing for the duration of such activation. Upon the removal of activation from this input, all portions which are timing, will certainly return to timing. During Quit Timing, car actuations on non-Green stages are identified; automobile actuations on Environment-friendly phase(s) reset the Passage Time timer in the typical manner, as well as the controller device does not end any interval or interval section or choose another phase, other than by activation of the Period Breakthrough input.
Only phases furnished for pedestrian solution are to be made use of in a non-actuated mode. Exterior Minimum, Recall to All Car Phases Places persisting need on all automobile stages for a minimum lorry service External Beginning Causes the controller system to revert to its configured initialization stage(s) as well as interval(s) upon application of the signal.
Stroll Relax Modifier When activated, click this link customizes non-actuated procedure just. Upon activation, the non-actuated stage(s) stay in the timed-out WALK state (remainder in stroll) in the lack of a functional contradictory call without regard to the Hold input status. With the input nonactive, non-actuated phase(s) do not remain in the timed-out WALK state unless the Hold input is active.
All About Safety Network
Some activated controllers provide an unique setting of procedure acquired from the Texas Division of Transport's historical approach to diamond interchange operation. Modern controllers can provide comparable functionality without the demand for a special setting of operation, as described in area 3.
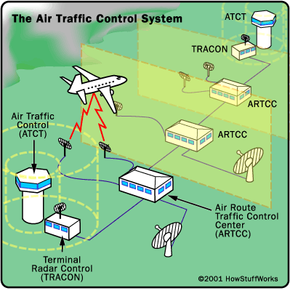
The 3-phase sequencing received Figures 7-6 as well as 7-7 can provide a much shorter cycle length than the 4-phase sequencing displayed in Figure 7-7. Texas DOT conducted a research in which the 2 phase series shown in figure 7-7 were contrasted at a number of crossways throughout isolated full-actuated control.
Anticipate comparable reductions in cycle lengths at locations in other isolated and interconnected systems, as long as the left-turn movements stay within affordable limitations, and also storage is available between the off-ramp (frontage road) links. Where transforming motions are high onto and/ or off of the ramp links (frontage roads), the 4-phase sequence offers the very best operation. https://s4fetynetw0rk.start.page/.
The 6-Second Trick For Safety Network
If the controller includes greater than one stage series, the sequences can be transformed to fit functional requirements (Traffic control companies). Procedure Summary Left-Turn Restoration In the procedure of a standard 8-phase controller unit, the solution of a left-turn can be brought back without first biking through the obstacle line. In this procedure, the controller device keeps an eye on the time remaining on any thru activity phase which is opposed by a thru stage which has gapped out.